Challenge 5 of CarolinaCon 9’s CTF started out with the following text:
Xrgling, the Hive is in an extremely volatile and perilous situation. We’ve tried expanding our creep on multiple occasions but we’ve run into heavy resistance at our expansion bases. Terran Ghosts have been using their cloaking ability to hide while killing our forces and we are losing ground rapidly.
To make matters worse our Overlords have not been able to geolocate their hideout yet so that we can put an end to their attacks. We believe the Ghosts are operating out of a commercial business; we must find it.
We may have a lead. One of our infested Terran spies recovered the contents of a Ghost’s laptop. We believe it contains evidence which could lead us directly to the Terran Ghost hideout. Search through the data. We must find the name of their cover operation!
The challenge provided us with the following memory dump available here.
After extracting the memory dump the first thing we did was fire up volatility and attempt to gather info about the memory dump with the following command:
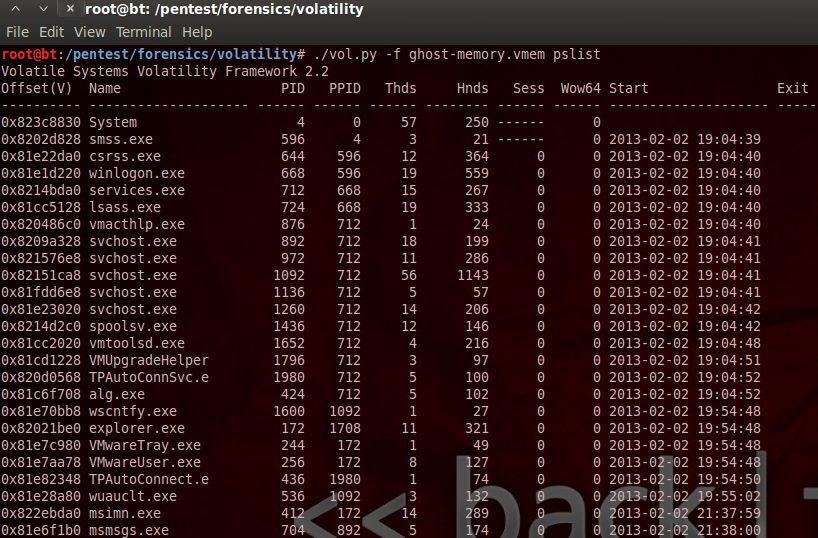
After determining that the memory dump is from a Windows machine, the first thing I wanted to do was perform a process listing and see what processes were running when the dump was made. This was done with the following command:
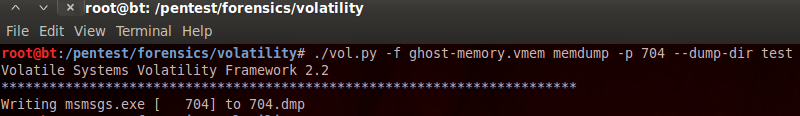
Upon looking at all the processes that were active, everything had looked pretty normal, but if I had to guess, and considering this is a CTF where I/we know something is wrong, I immediately suspected something might be held within the msimn.exe or more likely the msmsgs.exe process. I chose to look more into the msmsgs.exe process, and after some trying to determine the correct command, I dumped the memory specifically for msmsgs.exe with the following command:
With the process’s memory dumped to disk, I navigated into the test directory, and ran strings against the memory dump, and piped it into a different text file. Upon reviewing the text output, the following text can be found:
<HTML>
<HEAD>
<META HTTP-EQUIV=”Content-Type” CONTEN
#”text/html; charset=windows-1252″>
<META NAME=”Generator” CONTENT=”Internet Assistant for Word Version 3.0″>
</HEAD>
<BODY>
<FONT SIZE=2><P>Rookie,</P>
<P>You’ll be joining the Ghost Unit, they are THE elite Terran fighting force. The Zerg may be a tough enemy, but they are no match for our cloaking ability. You must be extra careful to ensure that those $
#ing Academy and Headquarters. 42.094513,-87.765462. See you soon.</P>
<P>- Jim</P>
</FONT></BODY>
</HTML>
Obviously, this is providing us with GPS coordinates to lookup, and Google Maps is our friend. When dropping the coordinates into Google Maps, and dropping into Street View, we see the following :
When reviewing the challenge itself, it asks us to identify the commercial business the Ghosts are operating out of.
After typing into the flag submission “Raynor Garage Doors” we are informed that we solved the challenge.